Cloud Services Security Policy
Cloud security policy questions.
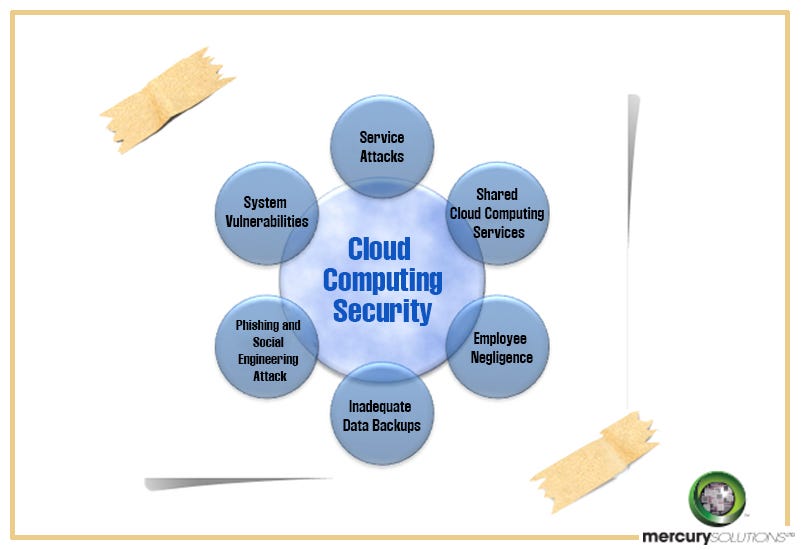
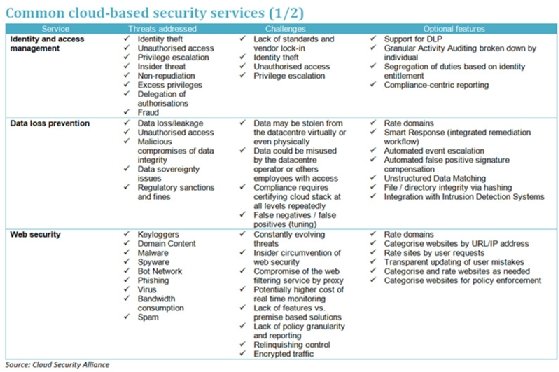
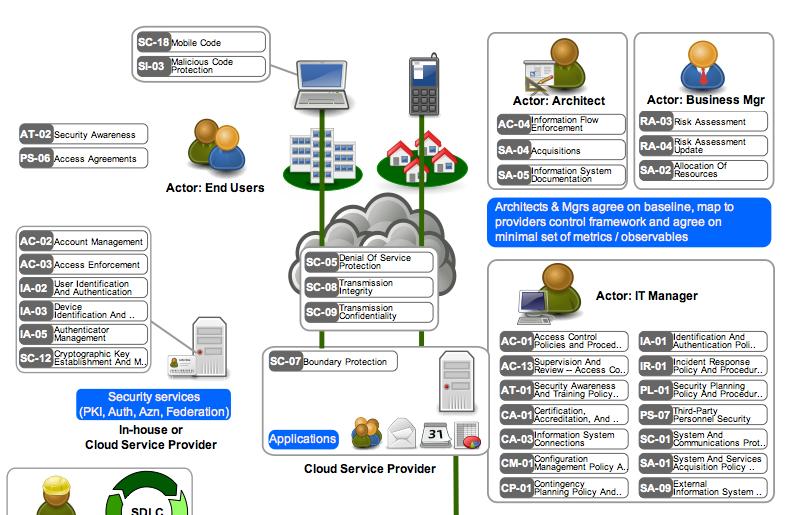
Cloud services security policy. Csp an entity private or public that provides cloud based platforms infrastructure application security or storage services for another entity organization. They include a suite of internal information security policies as well as different customer facing security practices that apply to different service lines. An architecture in which applications act as services on the internet. Before approaching a vendor you should be clarifying the answers to a few questions about the needs of your organization.
Usually for a fee. In this self paced course you will learn fundamental aws cloud security concepts including aws access control data encryption methods and how network access to your aws infrastructure can be secured. Cloud security consists of a set of policies controls procedures and technologies that work together to protect cloud based systems data and infrastructure. What types of cloud services will you be.
Their reasons for not liking the idea of hosting in a cloud are reliability and security. Usually for a fee. In this article the author explains how to craft a cloud security policy for managing. Some cloud based workloads only service clients or customers in one geographic region.
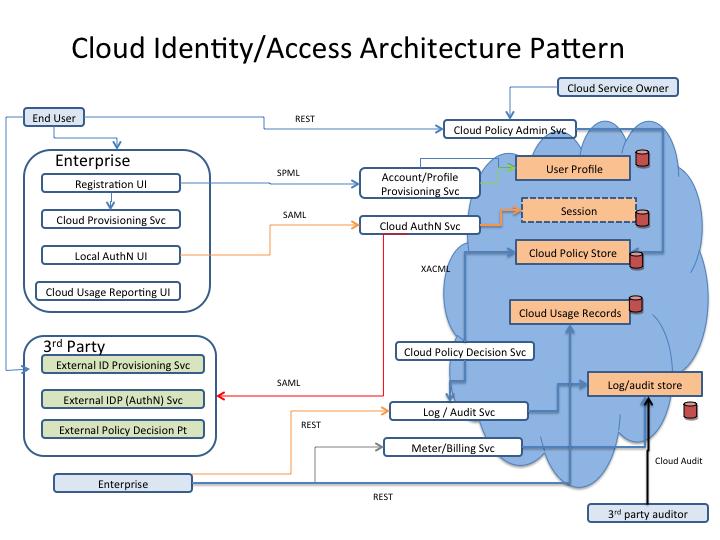
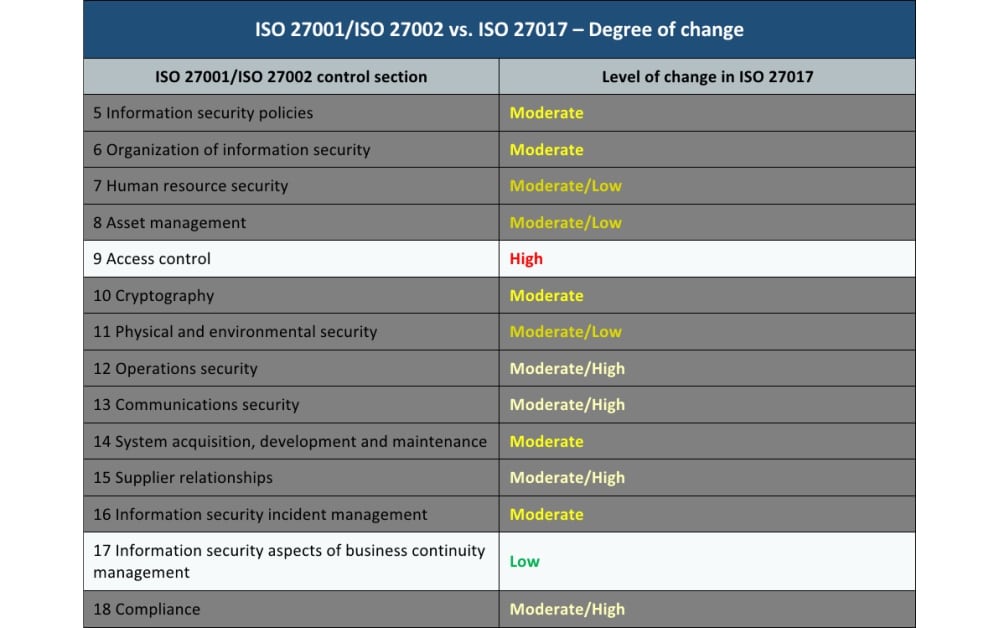
Csp an entity private of public that provides cloud based platforms infrastructure application security or storage services another entity organization. Cloud services policy page 5 that deviate from the suit security program policies are required to submit a policy exemption form to suit for consideration and potential approval. An architecture in which applications act as services on the internet. Oracle cloud security practices describe how oracle protects the confidentiality integrity and availability of customer data and systems that are hosted in the oracle cloud and or accessed when providing cloud services.
These cloud computing security measures are configured to protect data support regulatory compliance and protect customers privacy as well as setting authentication rules for individual users and devices. We will address your security responsibility in the aws cloud and the different security oriented services available. This policy applies to all persons accessing and using 3 rd party services capable of storing or transmitting protected or sensitive electronic data that are owned or leased by loyola university chicago all consultants or agents of loyola university chicago and any parties who are contractually bound to handle data produced by loyola and in accordance with. See 4 2 cloud service architecture csa.
Only open ports when there s a valid reason to and make closed ports part of your cloud security policies by default. For economic reasons often businesses and government agencies move data center operations to the cloud whether they want to or not. If the cloud provider makes it available use firewall software to restrict access to the infrastructure.